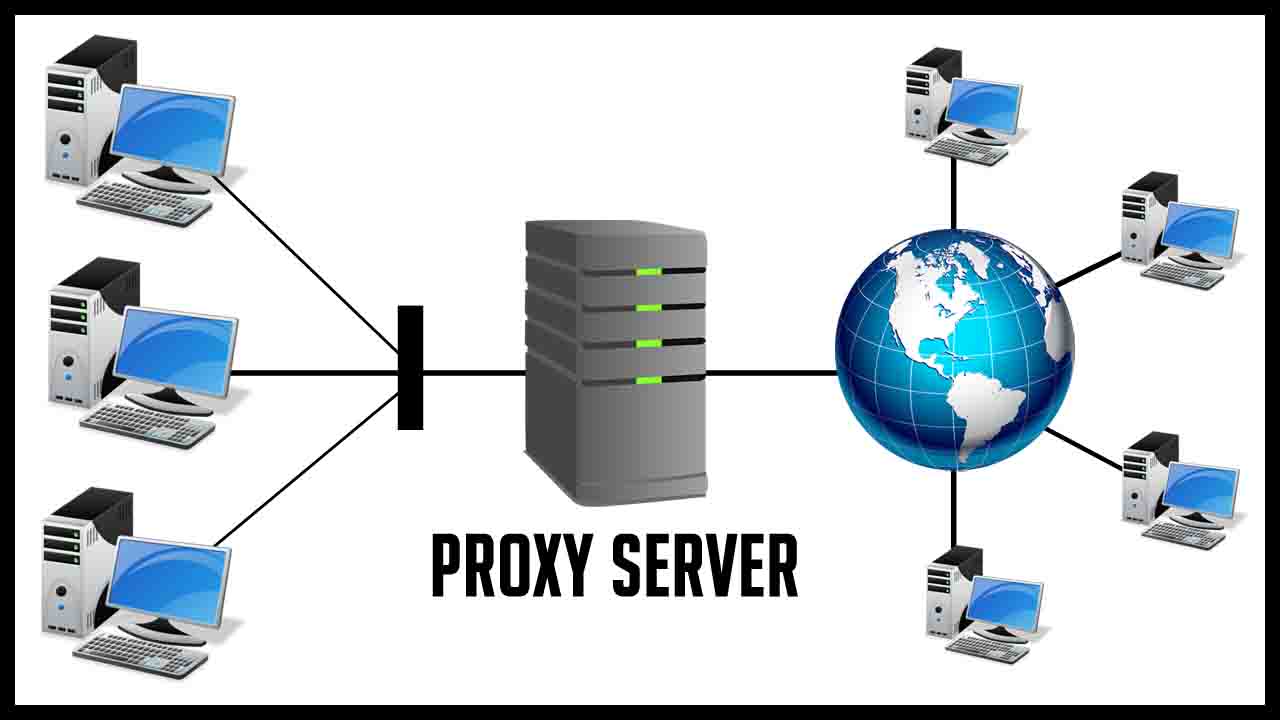
A proxy server acts as an intermediary between your device and the internet. Essentially, it serves as a gateway that facilitates communication between your computer and web servers. Instead of connecting directly, your requests pass through the proxy server, which then forwards them to the target server. This process masks your actual IP address, providing a layer of anonymity and security.
Proxy servers serve several purposes, including:
- Privacy and Anonymity: By using a proxy server, a user can hide their IP address from the websites they visit. This can help protect their privacy and make it more difficult for websites to track their online activities.
- Access Control: Proxy servers can be configured to restrict access to certain websites or content, making them useful for organizations that want to control or monitor internet usage within their network.
- Content Filtering: Proxy servers can filter content based on predefined rules. This is often used to block access to specific websites or content categories deemed inappropriate or unrelated to work in a corporate or educational environment.
- Load Balancing: In a network with multiple servers, a proxy server can distribute incoming requests among these servers, helping to balance the load and ensure efficient use of resources.
- Caching: Proxy servers can store copies of frequently requested resources locally. When a user requests a resource that is already in the proxy’s cache, the proxy can deliver it directly without needing to retrieve it from the internet again. This can improve speed and reduce bandwidth usage.
- Security: Proxy servers can add a layer of security by acting as a barrier between the user’s device and the internet. They can be configured to block malicious websites or content, helping to protect users from online threats.
When evaluating Proxy, there are several factors to consider:
Ease of use:
Proxy should provide a user-friendly interface that makes it easy to set up and configure proxies. It should have clear documentation and examples to help users get started quickly.
Performance:
Assess the performance impact of using Proxy. Evaluate factors such as latency, throughput, and resource usage to ensure that Proxy doesn’t significantly slow down your application or network.
Stability and maturity:
Assess the stability and maturity of Proxy by considering factors like its release history, versioning, and adoption by other developers. A mature and stable library is less likely to have critical bugs and is more likely to be actively maintained.
It’s important to note that evaluation criteria may vary depending on your specific use case and requirements.
Therefore, it’s recommended to try out Proxy and experiment with its features to determine if it meets your needs effectively.
Steps involved in setting up encryption and configuring a whitelist for a proxy server.
Account Encryption:
- Determine the encryption method: Choose an encryption algorithm such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman).
- Generate encryption keys: Use a cryptographic library or tool to generate the necessary encryption keys, including a public key for encryption and a private key for decryption.
- Implement encryption in your code: Use the chosen encryption algorithm and keys to encrypt sensitive data before storing or transmitting it.
- Implement decryption in your code: Use the private key to decrypt the encrypted data when it needs to be accessed.
Whitelist Configuration:
- Identify the IP addresses or domains to be whitelisted: Determine which IP addresses or domain names should be allowed access to your proxy server.
- Access the proxy server configuration: Depending on the proxy server software or framework you are using, locate the configuration file or settings.
- Configure the whitelist: Add the identified IP addresses or domain names to the whitelist configuration. This may involve modifying the configuration file or using a management interface provided by the proxy server software.
- Apply the changes: Save the configuration file or apply the changes through the management interface.
- Restart the proxy server (if necessary): In some cases, restarting the proxy server may be required for the changes to take effect.
Proxy is a Python library that provides proxy support for making HTTP requests. It does not specifically offer long-term or short-term IP features out of the box. However, you can use Proxy in conjunction with other tools or services to achieve your desired IP rotation functionality.
Certainly! Here are some potential advantages of using “proxy” in a concise manner:
Geographical Restrictions Bypass:
Allows you to access blocked or restricted content by routing your traffic through different locations.
Content Filtering and Security:
Filters and blocks unwanted websites or content, providing additional security measures.
Performance Optimization:
Improves browsing speed by caching frequently accessed resources.
Load Balancing and Scalability:
Distributes traffic across multiple servers, ensuring efficient resource utilization.
Monitoring and Logging:
Provides insights into user behavior and network activity for monitoring and auditing purposes.
Remember, these advantages may vary depending on the specific implementation and configuration of “proxy.”
Long-term IP and short-term IP
To implement long-term IP usage, you would typically need a dedicated proxy server or a pool of proxies with stable IP addresses. These proxies would remain constant over an extended period, allowing you to maintain a consistent IP for your requests. You can find various proxy’s providers online that offer long-term IP solutions.
For short-term IP rotation, you can utilize proxy’s rotation techniques. This involves using a pool of proxies and switching between them for each request or after a certain number of requests. There are proxy’s services available that offer rotating IP addresses, where the IP assigned to your requests changes periodically or after a certain duration.
Proxy’s can be integrated with these proxy’s services or proxy’s management tools to implement IP rotation. You would need to configure to use the proxy’s server or service of your choice and handle the rotation logic within your Python code.
Please note that the availability and specifics of long-term IP or rotating IP features may vary depending on the proxy’s service or provider you choose to work with. It’s recommended to refer to the documentation or support resources of the specific service or provider for detailed implementation instructions.
-1.png)